This website is maintained by Matti Nikki, a computer security researcher, and is written in response to the recent scandal in Britain about someone in the sex offender list being hired as a teacher. After some web searches, it turns out that the incident isn't quite so simple as it seems to be on the surface and there are things that need to be told.
Update 2006-04-05: I was informed related research on the subject, you can go view it here: Operation Ore - research.
Paul Reeve's name is all over the media now but only very few sites seem to describe what he did and how he got caught. One of the news articles describing the events is EDP24's article, "Sex case; Where the system went wrong". The interesting detail follows:
Reeve's name was one of around 7000 given to police in the UK after the US postal service smashed Texas-based website run by Landslide Productions. The names had been obtained from credit cards that had been used to pay to download the sick images of children.
The above quote reveals why he was under suspicion, but contains some wrong information. Not all people in the Landslide database were people accessing child pornography. I will get into details about this in the section about KeyZ.
It seems Mr. Reeve has claimed that he hasn't tried to intentionally access child pornography. What really happened is unclear, however he has apparently admitted to "incitement" as stated in Times Online article "Police challenge official excuse", and it says he had been charged of incitement and had admitted this and agreed to be cautioned. This doesn't, however, mean that he's guilty of anything.
Paul Reeve might be innocent and yet have taken the easy way out of the investigation. There's a video on channel4.com about another man who claims to be innocent, yet accepted the caution. Paul Reeve might've been under a strong pressure during the police investigation. Although the police found no evidence that he had downloaded anything, there might've been something the police found questionable given the context. This could've looked bad since he worked with children and the police might've threatened that the accusations be revealed to everyone. Taking the caution to get away with it might've seemed like a good idea at the time.
There are several sites on the net telling about the Landslide site. Save The Children mentions it in their position paper as well, and the official view to how the investigation went is summed up nicely on CBC's Landslide page. Lately, there's been reports and evidence that the Landslide investigation was flawed, as reported by Times Online in the article "A flaw in the child porn witch-hunt". The so called "smoking gun", a banner advertising for child porn on the Landslide page, was a rotating advertisement banner that didn't originate from Landslide at all. The 7200 UK names on the list also include people who were using the services of Landslide to access legit pornography, and the claims against Landslide are being questioned by many. A quote from the above article follows:
When police investigators found no evidence on seized computers, they did not assume the user might be innocent or had sought only legal, adult material. They were charged instead with “incitement”. These charges alleged that, simply by making a credit card payment through the internet, the child porn webmasters were encouraged to continue trafficking.
This is exactly what Paul Reeve is being accused of -- incitement. Although this doesn't prove his innocence, there doesn't seem to exist evidence of guilt either.
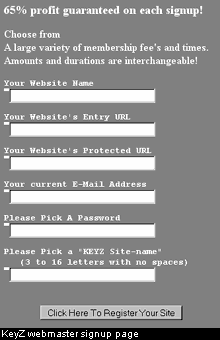
The core of this incident is child pornography, and that's where KeyZ.com comes into the picture, as that's what is being accused of being a child porn portal. The reality, however, appears different when the site is observer through Wayback Machine, a wonderful tool for researching history and cases like this. Wayback Machine has archived snapshots from countless websites at different days, so it's possible to go back and check what the sites in question looked like. Through here, the real nature of KeyZ.com is revealed.
KeyZ appears to have been a redirector and access control service. Anyone could have joined the system by merely entering a bunch of details in a form on a web page. Once the webmaster of a commercial site entered details of the site into KeyZ, Landslide would take care of billing and access control. The actual site itself would be left unprotected, to be accessed through the KeyZ gateway. There was no review, no human verification in the site registration, everything was automated. As a result of this, child porn website operators would just upload their pictures somewhere and register the site into KeyZ. Landslide would collect payments from users without ever knowing what the real site contains, and then would redirect the paying customers to the actual site. KeyZ didn't provide child porn, child porn sites merely chose to use the KeyZ automated access control and billing system to sell their content.
KeyZ gave simple instructions to would-be porn site administrators: Place the protected content into different directory and put a link pointing to KeyZ's login page on the site instead of linking to the protected content directly. The idea was, if the protected address leaked to larger audience, it could be changed at any time. KeyZ was the gateway which made sure only paying customers could find the secret directory. You can see the instructions in the KeyZ setup page yourself. (local mirror)
KeyZ expected that the login link is placed on an entry page of a porn site on the web, however in this case the problem of tracing the site wouldn't exist. Although I don't have solid evidence for it, it seems at least some sites that operated through KeyZ didn't provide entry page at all. The KeyZ-addresses were probably spammed in usenet and promoted as child porn there. In article from 2002, BBC News talks about Operation Avalanche: Tracking child porn. The image used for the article is displaying a usenet client, which further supports my hypothesis that KeyZ was being abused by child porn distributors. These third parties took advantage of this unintended design detail of how KeyZ hid the content's location prior to payment. This is what the police is talking about in the article:
Although the ring was technically operating through a "gateway" based in Texas, the material being accessed was sited around the world, principally Russia and Indonesia.
This arrangement made it far harder to crack than standard criminal operations as it was twice as hard for investigators to find out who was behind the websites.
So, essentially, KeyZ was a redirecting service much like many others that exist today, with the exception that it would only redirect users that chose to pay. In the Times Online article "A flaw in the child porn wicth-hunt" a British forensic computer consultant, Sam Type, who was asked by the National Crime Squad (NCS) to rebuild the Landslide website describes KeyZ as a "pay-per-view" service and dismisses the idea that it was devoted for child porn.
To put it another way, KeyZ was an attempt to implement hyperlinks that you could only follow if you paid.
If you used your credit card to buy access to any KeyZ enabled site, or someone else used your credit card information to buy access, you got into Landslide's customer list. This list is what was used to accuse people of viewing child pornography, even though you could've gotten on it for buying access to legitimate pornography.
The basis for assumption that everyone on the Landslide list had been downloading child porn is apparently a banner spotted on Landslide site advertising child porn. "Click here for child porn" banner did exist, but not where it was claimed to have been. It is unclear to me where exactly it was, but the investigators have admitted under oath that they only spotted it appearing once, at the very start of the investigation.
There is very little evidence against Paul Reeve. A name in Landslide list linking him to having used services of adult pornography billing system, and Reeve's agreement to be cautioned regarding the issue. This case urgently needs more evidence. Unless more evidence is released, it seems the reason he isn't allowed to teach is not because he's a risk to the children, but because he's a risk to the headmaster of the school and the officials at Education Department.
Based on evidence available, Landslide has been falsely accused of distributing child porn, and the evidence suggests that their system wasn't designed to faciliate that. Further, they're being held responsible for content they didn't see themselves at all. This is like suing an ISP for hosting illegal material instead of working with them to remove it and trace the person who uploaded it. I dont think it would've been very difficult for the police to ask Landslide to give them access to their KeyZ databases.
Comments? Feedback? If you have any additional information on anything presented on this page, do contact. I'll be happy to correct any possible errors presented on this page and to amend my opinions on both Reeve and Landslide should there be a reason to do so.
2006-01-14 Matti Nikki <muzzy@iki.fi>